Competition basics
Teams compete in three divisions:
- Open High School Division:
Open to all high schools, scouting units, Boys and Girls Clubs, and
approved high school home school programs across the country
- All Service Division: High school JROTC Programs / Civil Air Patrol units / Naval Sea Cadet Corps units
- Middle School Division: Open to teams of middle school students
The
early rounds of the competition are done online during weekends in a
six-hour period from the teams' home locations (schools, homes,
libraries, etc.). A Coach chooses their team's six-hour competition
period.
Each team has two challenges during their six-hour competition period:
- The Network Security Challenge involves finding and fixing security vulnerabilities in Windows and Linux operating systems.
- The Cisco Networking Challenge consists of an online quiz and a virtual networking exercise based on specific training material
 Network Security Challenge Cisco Networking Challenge
Network Security Challenge Cisco Networking Challenge
The challenges are relatively easy in the first round and become more complex as the competition continues.
Before the round
- Train: Teams should start training for the competition as soon as they can before the first round. Updated training materials are on the dashboard that Coaches and Mentors see upon signing into the website. These training materials are a great place to start, but they do not cover everything. Teams should rely on their Technical Mentors to receive more advanced training. Archived training materials are available on the public side of the website. The Cisco Networking Academy (NetAcad) will have a Content (Training) Course) available in September that will be used for the the Cisco Networking Challenge. Login credentials for NetAcad will be available when the training materials are posted.
- Prepare: All teams should make sure that they have the hardware, software, and network capabilities required to compete successfully. As the goal of the program is to have as many teams as possible competing, technical requirements are kept to a minimum.
- Download : About a week before the competition begins, the CyberPatriot Program Office sends an email with round instructions and links to download the virtual machine images (operating systems that can be played on top of other operating systems). These files are very large and should be downloaded and well before a team is ready to compete. Teams also verify that their download was successful before the round begins. There are usually two or three images per round.
During the round
- Extract : In the morning of the Friday of the competition weekend, teams receive an email with the password to extract the virtual machine images from their downloads. After doing so, they can load the images in VMware Player and begin competing.
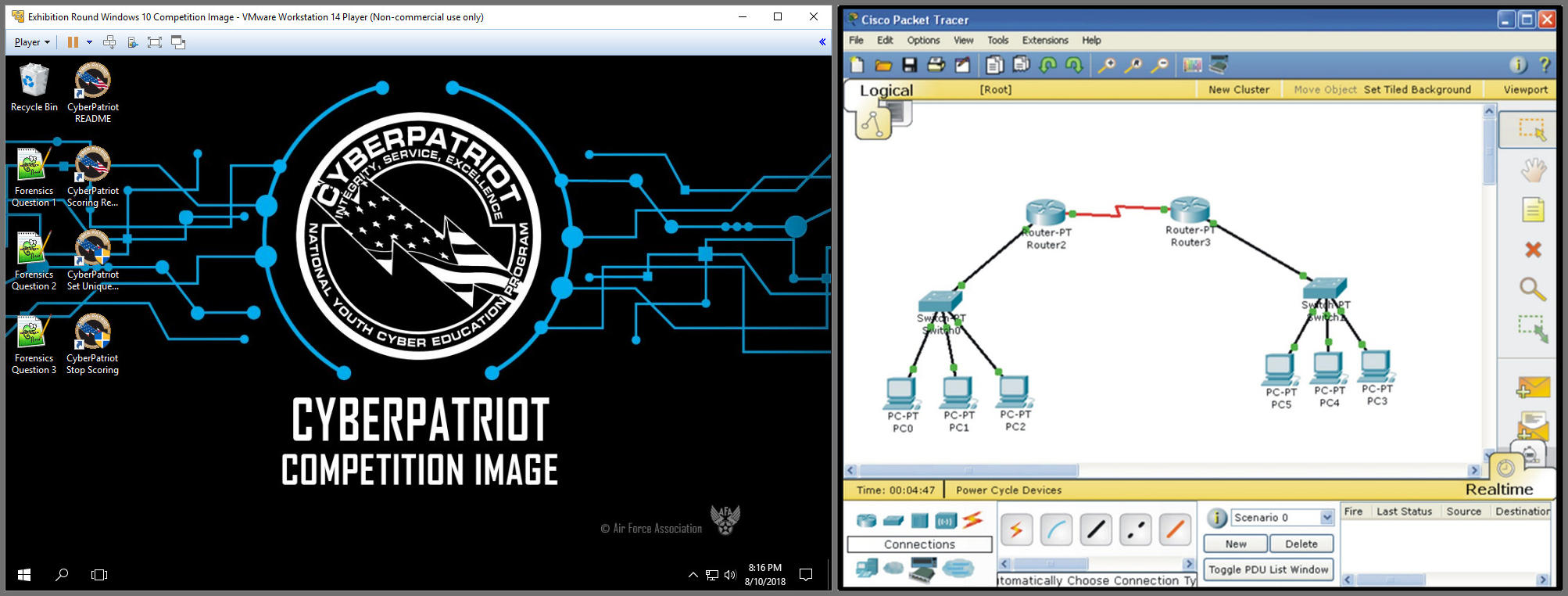
- Identify : When the images are opened, teams are prompted to enter a Team ID. This is a twelve-digit alphanumeric code that is assigned to teams and posted on their Coach's Dashboard which is found on the CyberPatriot website.
Team Unique ID Box on a Virtual Machine Image
- Fix: The goal of every CyberPatriot competition is to find and fix vulnerabilities in their images. These images range from simple (e.g. giving users strong passwords) to much more complex. Some rounds also include networking challenges in the form of quizzes and Cisco Packet Tracer activities. Teams can also gain points by answering questions about their actions on the image.
- Score : When teams fix a vulnerability that is being checked, they receive points. If they take an action that makes a system less secure, they lose points. Teams can also gain points by answering forensics questions about actions they took to solve their vulnerabilities. Teams can check their progress on their score report page.
Score Report Page
- Compare: A live scoreboard is available for teams to see how they stack up against others in the country. These scores are unofficial and undergo review by CyberPatriot staff following the competition.
Public Scoreboard
Log In: To access the Cisco Networking Challenge, teams must login to the competition Course at www.netacad.com. The course must be completed in the same six hour competition period as the images.
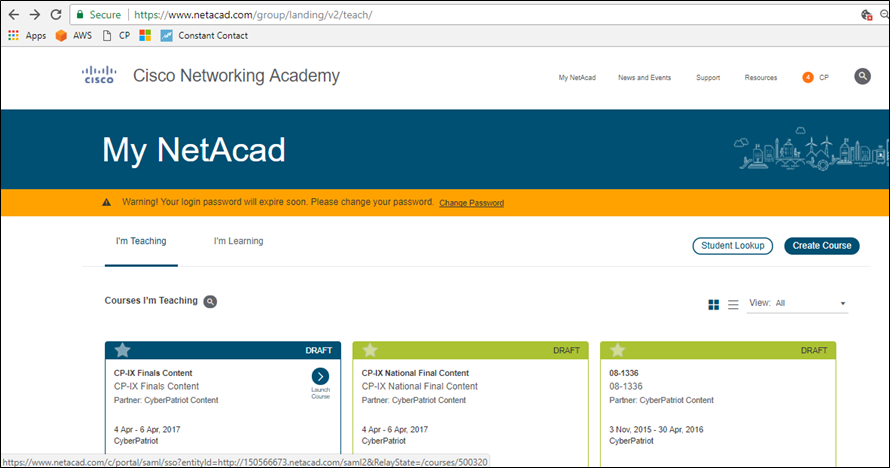
Cisco Networking Academy Competition Course
Open: Once logged into their Networking Academy Accounts, teams must open and compete on the Cisco Networking Quiz and Packet Tracer exercise for the round. The Cisco NetAcad Content (training) Course will cover the subject matter used for the quiz and exercise.
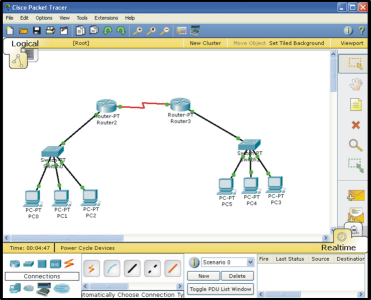
Cisco Packet Tracer
Ask: CyberPatriot staff is available to answer technical support questions during the round by chat and by phone at 877-885-5716 during peak competition hours. Instructions for accessing the tech support chat are sent to teams at the beginning of each round. Teams may not ask questions about vulnerabilities during the technical chats.
After the Round
- Delete: All virtual machine images should be deleted after the round is over to maintain the integrity of the competition.
- Wait: CyberPatriot staff reviews all the scores following the competition and releases official scores and standings to teams within a week after the round is over.
Have technical questions about the competition? Contact cpoc@uscyberpatriot.org.